We at WeSoftYou understand the importance of building secure decentralized apps. With the rise of blockchain technology and the growing popularity of decentralized applications (dApps), it has become crucial to prioritize security in app development. In this article, we will discuss the key practices that senior-level executives like founders, CTOs, and CEOs should follow to ensure the security of their decentralized apps.
Understanding Decentralized Apps
Decentralized apps, or dApps, are applications built on decentralized networks like blockchain. Unlike traditional apps that rely on centralized servers, dApps leverage the power of a distributed network to operate efficiently and securely. They offer transparency, immutability, and trustworthiness by eliminating the need for intermediaries and enabling direct peer-to-peer interactions.
From our experience, it’s crucial to have a clear understanding of decentralized apps before diving into their development process. This includes grasping the concept of blockchain technology and its underlying principles. It is also essential to comprehend the potential benefits and limitations of dApps for your specific use case.
What are Decentralized Apps?
Decentralized apps, as the name suggests, are applications that are decentralized and run on a distributed network rather than a central server. These apps leverage blockchain technology and smart contracts to facilitate secure and transparent transactions.
One of the key advantages of decentralized apps is their ability to provide a high level of transparency. Since all transactions are recorded on the blockchain, anyone can verify and audit the data. This transparency fosters trust among users and eliminates the need for intermediaries, such as banks or payment processors, to validate transactions.
Moreover, decentralized apps offer immutability, meaning that once a transaction is recorded on the blockchain, it cannot be altered or tampered with. This feature ensures the integrity of the data and prevents fraudulent activities.
Another significant benefit of dApps is their potential to revolutionize various industries. For example, in the financial sector, decentralized apps can enable peer-to-peer lending, eliminating the need for traditional banks and reducing transaction costs. In supply chain management, dApps can provide end-to-end visibility, ensuring the authenticity and traceability of products.
Importance of Security in Decentralized Apps
Security is vital in decentralized apps due to their unique characteristics. As dApps are built on blockchain networks, which are inherently immutable, any security vulnerabilities or weaknesses could have severe consequences. From financial transactions to data storage, security breaches can result in the loss of sensitive information, financial assets, and the trust of users.
To ensure the security of decentralized apps, developers must follow specific principles and best practices. One of the fundamental principles is the use of cryptographic techniques to protect sensitive data. Encryption algorithms and digital signatures can safeguard transactions and ensure that only authorized parties can access the information.
Another crucial aspect of dApp security is the implementation of robust smart contracts. Smart contracts are self-executing agreements that automatically enforce the terms and conditions of a transaction. However, if not properly coded, smart contracts can be vulnerable to attacks. Therefore, developers must conduct thorough testing and auditing to identify and fix any potential vulnerabilities.
Furthermore, decentralized apps should also consider the security of the underlying blockchain network. This includes ensuring the consensus mechanism is robust and resistant to attacks, implementing proper access controls, and regularly updating the software to patch any known security vulnerabilities.
In conclusion, decentralized apps offer numerous advantages over traditional centralized applications. They provide transparency, immutability, and trustworthiness by leveraging the power of blockchain technology. However, it is crucial to prioritize security in dApp development to protect sensitive data, financial assets, and the trust of users. By following best practices and implementing robust security measures, developers can create secure and reliable decentralized apps that have the potential to transform various industries.
Key Principles of Secure Decentralized App Development
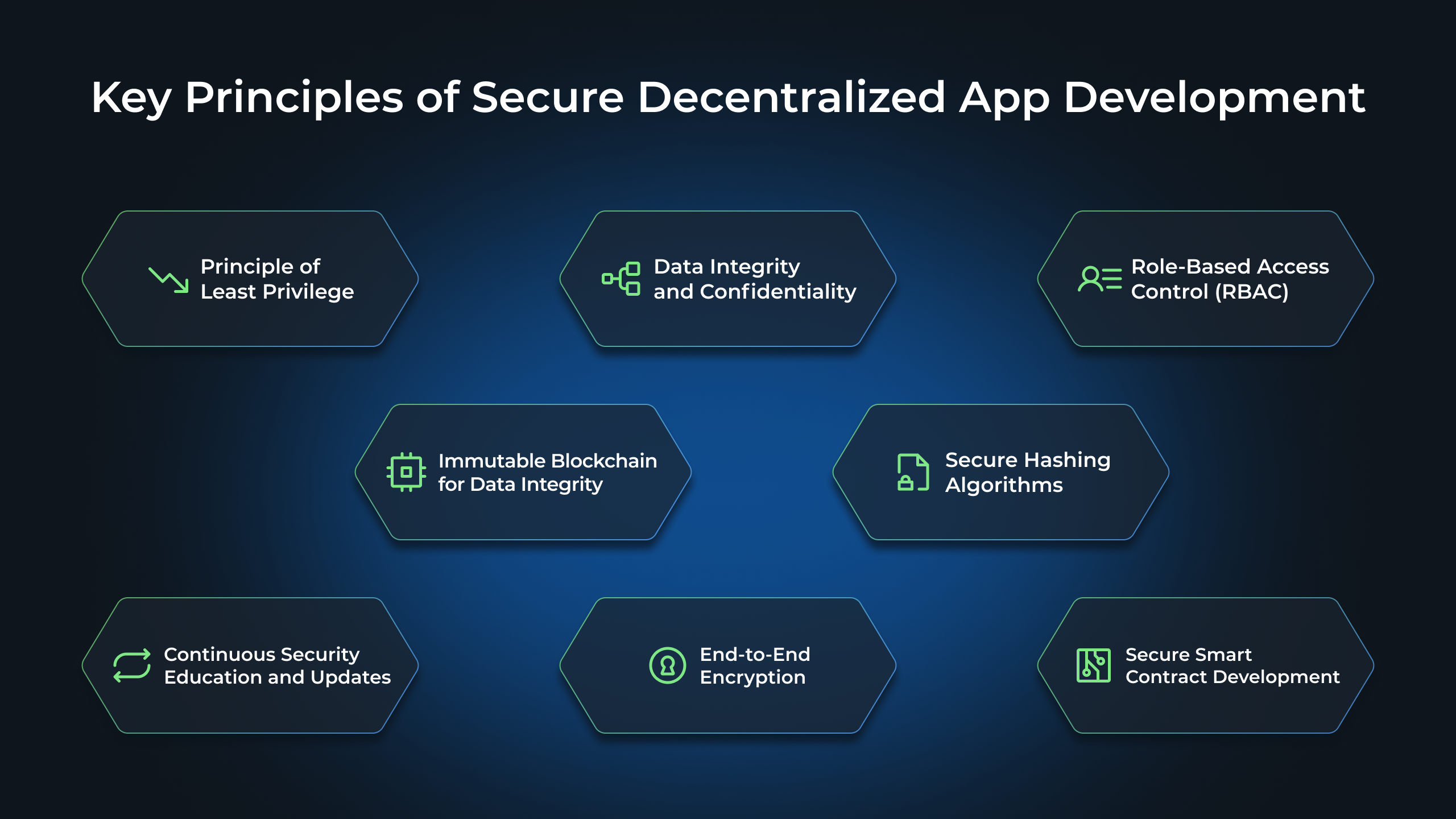
Decentralized app development has become increasingly popular in recent years, thanks to the numerous benefits it offers, including enhanced security and transparency. However, ensuring the security of decentralized apps requires following key principles that govern secure development practices. In this article, we will explore two of these principles: the Principle of Least Privilege and Data Integrity and Confidentiality.
Principle of Least Privilege
The principle of least privilege is a fundamental concept in cybersecurity that states that individuals should only have access to the resources and information necessary to fulfill their roles. This principle applies to decentralized app development as well.
By implementing the principle of least privilege, app developers can limit the potential damage caused by compromised accounts or malicious actors. This involves granting users and smart contracts only the permissions required to perform their tasks, reducing the attack surface and minimizing the impact of security breaches.
For example, in a decentralized finance (DeFi) app, users may have different roles, such as traders, liquidity providers, or administrators. Each role should have specific permissions and access rights tailored to their responsibilities. By strictly adhering to the principle of least privilege, developers can ensure that users and smart contracts can only perform actions that are necessary for their designated roles, reducing the risk of unauthorized access or malicious activities.
Data Integrity and Confidentiality
Ensuring the integrity and confidentiality of data is crucial in decentralized app development. Blockchain networks provide immutability, but it’s essential to encrypt sensitive data to protect it from unauthorized access and tampering.
Developers should implement robust encryption algorithms and mechanisms to safeguard user data. By employing techniques like asymmetric encryption and secure hashing, they can maintain the confidentiality and integrity of sensitive information, such as personal details, financial transactions, and intellectual property.
For instance, in a decentralized messaging app, user messages need to be encrypted to prevent eavesdropping and unauthorized access. By using strong encryption algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), developers can ensure that the content of the messages remains confidential and cannot be deciphered by unauthorized parties.
Additionally, developers should also consider implementing mechanisms to verify the integrity of data stored on the blockchain. This can be achieved through the use of cryptographic hashes, which generate unique fingerprints for data. By comparing the computed hash of a piece of data with its stored hash on the blockchain, developers can detect any tampering attempts and ensure the integrity of the stored information.
By following the principles of least privilege and ensuring data integrity and confidentiality, developers can build secure decentralized apps that protect user information and maintain the trust of their users. However, it’s important to note that these principles are just the tip of the iceberg when it comes to secure app development. Developers should continuously stay updated with the latest security practices and technologies to effectively mitigate emerging threats and vulnerabilities.
Steps to Building Secure Decentralized Apps
Designing a Secure Architecture
A secure architecture is the foundation of any decentralized app. It involves planning and designing the app’s components, networks, and protocols while keeping security in mind.
During the design phase, developers should consider potential attack vectors and implement preventive measures to mitigate them. Network segmentation, strong authentication mechanisms, and secure communication protocols ensure a robust and secure architecture.
One important aspect of designing a secure architecture is considering the different layers of the app. Each layer, such as the presentation layer, application layer, and data layer, should be designed with security in mind. For example, the presentation layer should have proper input validation to prevent common attacks like cross-site scripting (XSS) and SQL injection.
Furthermore, the application layer should implement secure coding practices to handle authentication securely. This includes using strong encryption algorithms, securely storing passwords, and implementing multi-factor authentication where appropriate.
The data layer is another critical component that requires careful consideration. Developers should implement secure data storage practices, such as encrypting sensitive data at rest and in transit, to protect user information from unauthorized access.
Additionally, during the design phase, it is important to consider the scalability and performance of the decentralized app. By implementing proper load balancing mechanisms and optimizing the code, developers can ensure that the app remains secure even under heavy traffic.
Implementing Secure Coding Practices
Secure coding practices play a significant role in building secure decentralized apps. Developers should follow industry-standard guidelines and adopt secure coding frameworks to minimize the risk of vulnerabilities and security breaches.
From our experience, ensuring proper input validation, handling authentication securely, and implementing secure data storage practices are essential for secure decentralized app development. Thorough code reviews and regular security assessments can help identify and mitigate potential security flaws.
Another important aspect of secure coding practices is keeping up with the latest security updates and patches. By regularly updating the app’s dependencies and libraries, developers can address any known vulnerabilities and ensure that the app remains secure against emerging threats.
Furthermore, developers should implement strong access controls to restrict unauthorized access to sensitive resources. This includes implementing role-based access control (RBAC) and regularly reviewing and revoking unnecessary privileges.
Secure coding practices also involve proper error handling and logging. By implementing comprehensive error handling mechanisms, developers can prevent sensitive information from being exposed to potential attackers. Additionally, logging security-related events can help in identifying and investigating potential security incidents.
Lastly, developers should prioritize user education and awareness. By providing clear and concise instructions on security best practices, such as using strong passwords and being cautious of phishing attempts, developers can empower users to protect their own data and contribute to the overall security of the decentralized app.
Testing and Auditing Decentralized Apps
Role of Penetration Testing
Penetration testing, commonly known as ethical hacking, is a critical step in ensuring the security of decentralized apps. It involves conducting controlled attacks to identify vulnerabilities and assess the resilience of the app against real-world threats.
During penetration testing, skilled security professionals simulate various attack scenarios to uncover security weaknesses, misconfigurations, or coding errors that could potentially be exploited by malicious actors. By actively seeking out vulnerabilities, businesses can proactively identify and address security risks before they can be exploited.
One common type of penetration testing is called “black box testing,” where the tester has no prior knowledge of the app’s internal workings. This approach allows for a realistic assessment of the app’s security posture, as it simulates the perspective of an external attacker.
Another approach is “white box testing,” where the tester has full access to the app’s source code and internal infrastructure. This method allows for a more in-depth analysis of the app’s security controls and can uncover vulnerabilities that may not be apparent from an external perspective.
Importance of Regular Audits
Regular audits are essential to maintain the security of decentralized apps. As the threat landscape evolves, new vulnerabilities emerge, making it crucial to conduct thorough audits at regular intervals.
During audits, security experts analyze the code, infrastructure, and configurations, ensuring compliance with security best practices. They review the app’s architecture, network configurations, access controls, and encryption mechanisms to identify any potential weaknesses.
Audits also involve examining the app’s dependencies, such as third-party libraries or frameworks, to ensure they are up to date and free from known vulnerabilities. Additionally, experts may review the app’s logging and monitoring systems to ensure that any potential security incidents can be detected and responded to promptly.
By conducting regular audits, developers can gain a comprehensive understanding of their app’s security posture and identify any gaps or weaknesses that may have been missed during the development and testing phases. Addressing these issues promptly helps strengthen the overall security of decentralized apps and enhances their resilience against potential attacks.
Ongoing Maintenance and Updates
Ensuring the security of decentralized apps is an ongoing process that requires developers to stay vigilant and proactive. In addition to implementing initial security measures, developers must also keep up with the latest security trends, vulnerabilities, and best practices.
Keeping Up with Security Trends
The field of cybersecurity is constantly evolving, with new threats and attack vectors emerging regularly. To effectively protect decentralized apps, developers need to stay informed about these evolving trends. By staying updated, developers can adapt their security measures and protect their apps from emerging threats.
One way developers can stay informed is by actively participating in security-focused online communities. These communities provide a platform for developers to share knowledge, discuss security challenges, and learn from each other’s experiences. By engaging with other experts in the field, developers can gain valuable insights into the latest security trends and strategies.
In addition to online communities, attending conferences and workshops dedicated to cybersecurity can also be beneficial. These events often feature presentations by industry experts who share their knowledge and insights. Developers can learn about the latest vulnerabilities, attack techniques, and best practices in securing decentralized apps.
Regular Patching and Updates
While implementing robust security measures is crucial, it’s equally important to regularly patch and update decentralized apps. Vulnerabilities can be identified during security audits, penetration testing, or even reported by users. Developers should promptly address these vulnerabilities to maintain the security of their apps.
One effective way to address vulnerabilities is by regularly updating libraries, dependencies, and framework versions. By keeping these components up to date, developers can fix known vulnerabilities and prevent potential exploits. It’s important to stay informed about security patches released by the developers of these components and apply them promptly.
Furthermore, maintaining the security of decentralized apps also involves applying patches and updates to the underlying blockchain network and smart contracts. Blockchain networks are constantly evolving, and new security features and improvements are regularly introduced. Developers must stay updated with these changes and apply relevant updates to ensure the overall security of their apps.
In conclusion, ongoing maintenance and updates are essential for maintaining the security of decentralized apps. By staying informed about the latest security trends, vulnerabilities, and best practices, developers can adapt their security measures to protect against emerging threats. Regular patching and updates, both at the app level and the underlying blockchain network level, are vital to address vulnerabilities and ensure the overall security of decentralized apps.
Overcoming Common Security Challenges
Ensuring the security of decentralized app development is crucial in today’s digital landscape. One of the most significant security challenges in this field is smart contract vulnerabilities. Smart contracts, built on blockchain networks, can be exploited if not implemented securely.
Developers should prioritize secure smart contract development by utilizing audited and well-tested smart contract templates or leveraging professional smart contract development services. These templates and services provide a solid foundation for building secure smart contracts, reducing the risk of vulnerabilities.
Regular code reviews and third-party audits are essential in identifying and rectifying vulnerabilities in smart contracts. By conducting thorough reviews and audits, developers can ensure the security of the decentralized app and protect users from potential exploits.
Dealing with Smart Contract Vulnerabilities
Smart contract vulnerabilities can have severe consequences, compromising the integrity and security of decentralized apps. It is crucial to address these vulnerabilities proactively to maintain the trust and confidence of users.
One effective approach to mitigating smart contract vulnerabilities is to follow best practices and industry standards. Developers should adhere to secure coding practices, such as input validation and proper error handling, to prevent common vulnerabilities like reentrancy attacks and integer overflow.
Additionally, utilizing audited and well-tested smart contract templates can significantly reduce the risk of vulnerabilities. These templates have undergone rigorous testing and auditing processes, ensuring their reliability and security.
Mitigating Front-End Risks
Front-end risks pose another significant security challenge in decentralized app development. Cross-site scripting (XSS) and clickjacking attacks are common vulnerabilities that can expose users to various security risks.
To mitigate these risks, developers should implement proper input validation and output encoding techniques. By validating and sanitizing user input, developers can prevent malicious code from being executed on the app’s front-end.
Implementing effective security headers is also crucial in protecting decentralized apps from front-end vulnerabilities. These headers can prevent clickjacking attacks by ensuring that the app’s content is displayed within a secure frame.
Furthermore, utilizing security-focused frameworks and libraries can significantly reduce the risk of front-end vulnerabilities. These frameworks and libraries often come with built-in security features and protections, making it easier for developers to create secure user interfaces.
However, it’s not enough to rely solely on technical measures. Educating users about potential risks and encouraging them to exercise caution while interacting with the app’s user interface is equally important. By promoting user awareness and responsible usage, developers can create a safer environment for users.
Future of Secure Decentralized Apps
Emerging Technologies and Techniques
The future of secure decentralized apps looks promising, with emerging technologies and techniques aiming to enhance their security. Techniques like zero-knowledge proofs, multi-party computation, and homomorphic encryption offer advanced security measures for decentralized app development.
Additionally, the integration of artificial intelligence (AI) and machine learning (ML) technologies can enhance the detection of anomalous behaviors, potential vulnerabilities, and security threats within decentralized apps, allowing for proactive security measures.
The Role of AI and Machine Learning in Security
AI and machine learning have the potential to revolutionize the security landscape of decentralized apps. These technologies can analyze vast amounts of data, identify patterns, and detect anomalies that might indicate potential security breaches or attacks.
By leveraging AI and machine learning algorithms, developers can build intelligent security systems that continuously monitor the app’s network, detect unauthorized access attempts, and quickly respond to emerging threats.
In conclusion, building secure decentralized apps requires a comprehensive understanding of decentralized technology, adherence to best practices, and regular security assessments. By following the key principles discussed in this article, senior-level executives can ensure the security, integrity, and confidentiality of their decentralized apps. We at WeSoftYou have extensive experience in software development, including decentralized apps. Contact us for a free consultation or project estimation and let us help you build secure and innovative decentralized apps.
FAQ
Decentralized apps, or dApps, are applications that are decentralized and run on a distributed network rather than a central server. These apps leverage blockchain technology and smart contracts to facilitate secure and transparent transactions.
Security is vital in decentralized apps due to their unique characteristics. As dApps are built on blockchain networks, which are inherently immutable, any security vulnerabilities or weaknesses could have severe consequences. From financial transactions to data storage, security breaches can result in the loss of sensitive information, financial assets, and the trust of users.
To ensure the security of your decentralized app, it is crucial to follow key principles such as the principle of least privilege and prioritize data integrity and confidentiality. Additionally, designing a secure architecture, implementing secure coding practices, and regularly testing and auditing your app are essential steps to enhance its security.
In decentralized app development, common challenges include smart contract vulnerabilities and front-end risks such as cross-site scripting attacks. It is important to mitigate these risks by following best practices, conducting regular code reviews, and keeping up with the latest security trends.