With the growing popularity of blockchain-based products, the need for impeccable security in DeFi keeps growing. As a result, while such solutions become more critical for banks and financial startups, ensuring their protection is more challenging. According to CipherTrace’s Q3 2020 Cryptocurrency Anti-Money Laundering (AML) report, hackers stole around $100 million from DeFi projects in 2020 alone.
With that alarming statistics in mind, it’s crucial to double-check the security measures when building a DeFi project. But how to make your product reliable enough in the first place? How can you enhance your solution’s defenses, and who can assist you in this task?
Luckily, there are stones to kill all of the mentioned birds. After completing numerous blockchain projects and providing Web3 software development services for multiple companies, the WeSoftYou team has developed a deep understanding of DeFi security best practices when building a blockchain project. Working with decentralized finance for over three years, we fully grasped the potential security issues of blockchain development. In this article, we will share our experience and discuss how to ensure DeFi security, provide measures to mitigate potential risks and improve your existing system.
Key Security Practices When Building a Blockchain Project
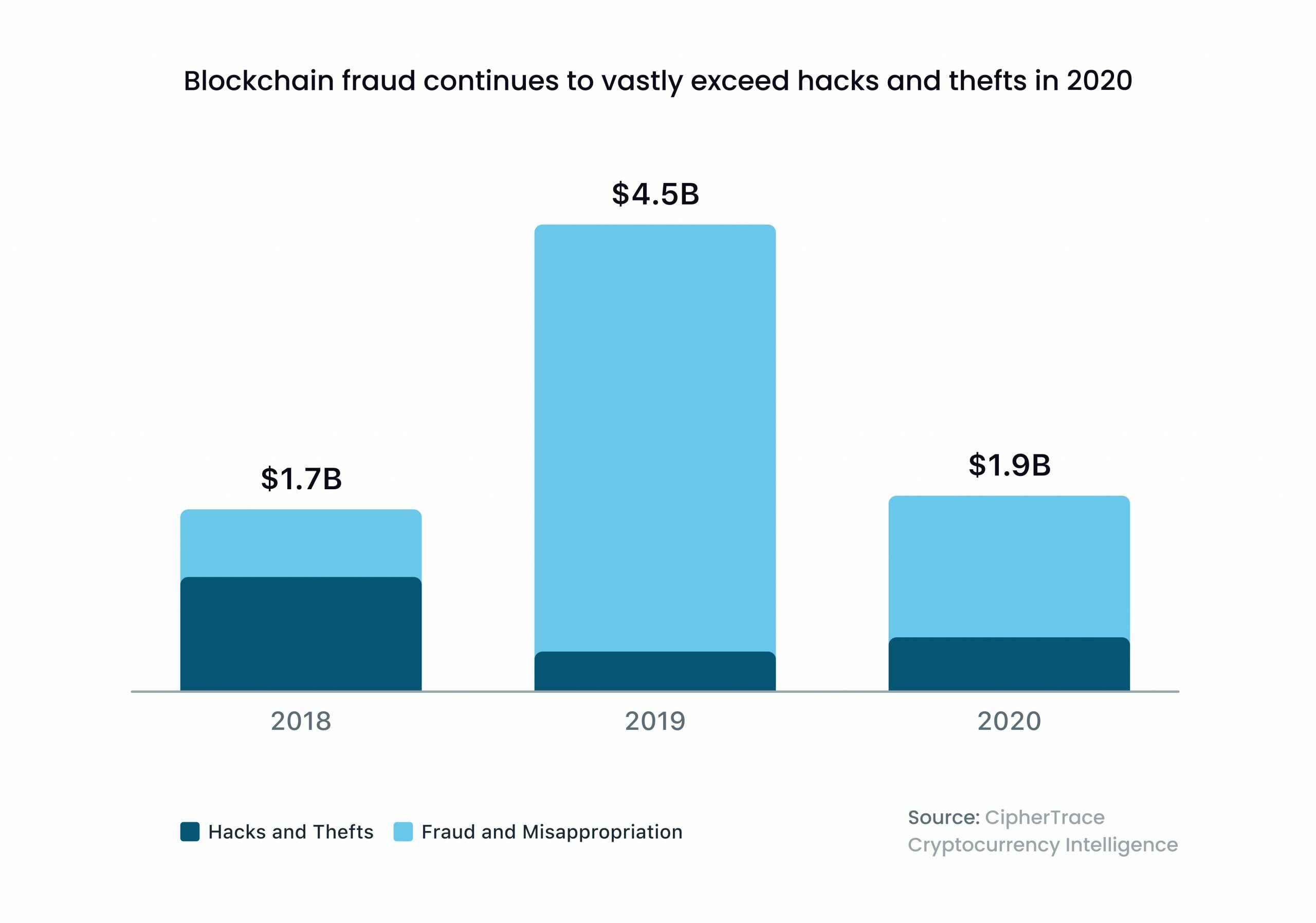
The above-mentioned report by CipherTrace showed $1.9 billion in significant cryptocurrency thefts, hacks, and frauds in 2020. In fact, it’s the second-highest annual value of crypto crimes ever recorded. This data signifies the known fraudsters’ appetite for Web3’s economic potential – and is a wake-up call to enhance your dApp’s security measures.
The prevalence of risks in DeFi protocols indicates that dApps may have significant vulnerabilities. In particular, the complexity of security risks and the ever-evolving Web3 landscape present new threats to DeFi. However, you can mitigate such issues by sticking to DeFi security best practices when building a blockchain project. Let’s review the seven essential approaches in more detail.
1. Testing & Static Analysis Tool
Testing and static analysis tools identify blockchain projects’ potential vulnerabilities and security risks. Thus, developers can fix issues before hackers find ways to exploit them.
During testing, experts verify whether a blockchain application functions correctly and securely. This process includes unit tests (components shown in the picture below), integration tests, and end-to-end tests. These methods ensure that the code functions as intended and there are no security pitfalls.
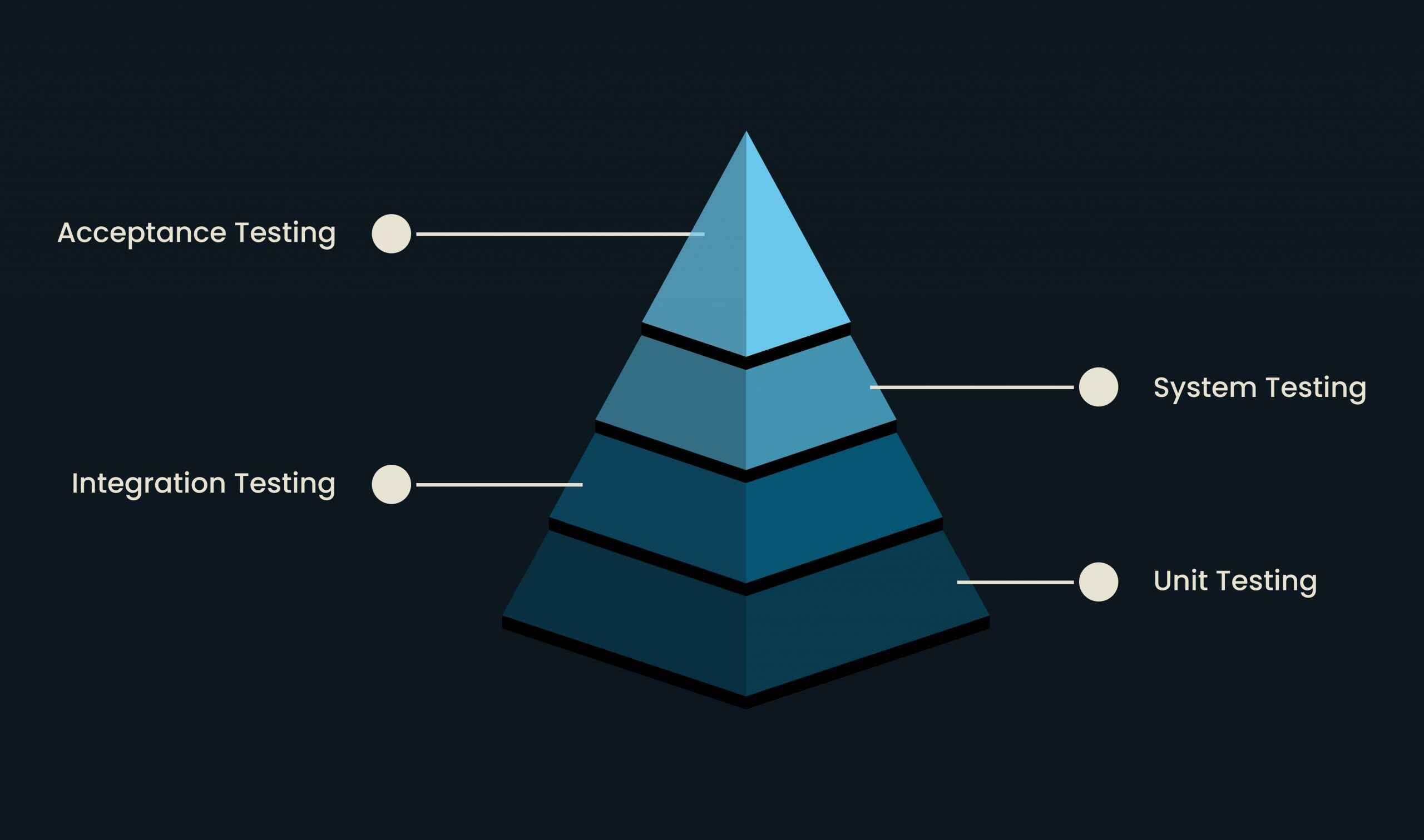
Note that it’s critical to test for functional and non-functional requirements, such as performance and security.
Another good tip is to use static analysis tools to scan the codebase for potential vulnerabilities and security risks. Such tools identify issues like buffer overflows, SQL injection, and cross-site scripting (XSS) attacks. If developers spot and address these problems early on, they can prevent significant security risks in the future.
Therefore, when building a Web3 project, testing and static analysis tools are vital. That’s because blockchain applications involve complex smart contract codes you should carefully audit. And these tools are your best bet to confirm that the codebase is secure and functions appropriately.
2. Frequently Made Mistakes Fixing
The overview of recommended DeFi security practices focuses on typical bugs in the smart contract code. If your product doesn’t follow the basic security standards, your technical team risks introducing more bugs into the code.
One common mistake is implementing improper access controls. It allows unauthorized users to access sensitive information or manipulate a blockchain application. To fix such an issue, the engineering team should provide appropriate access controls. For instance, you can use multi-factor authentication and implement role-based access management.
Another possible slip is incorrectly validated input. This flaw may lead to SQL injection and buffer overflow attacks. To avoid such outcomes, check if all user input corresponds to valid formats and doesn’t contain malicious code.
The third widespread mistake is taking incorrect user data security measures. This challenge results in data breaches and unauthorized access to sensitive information.
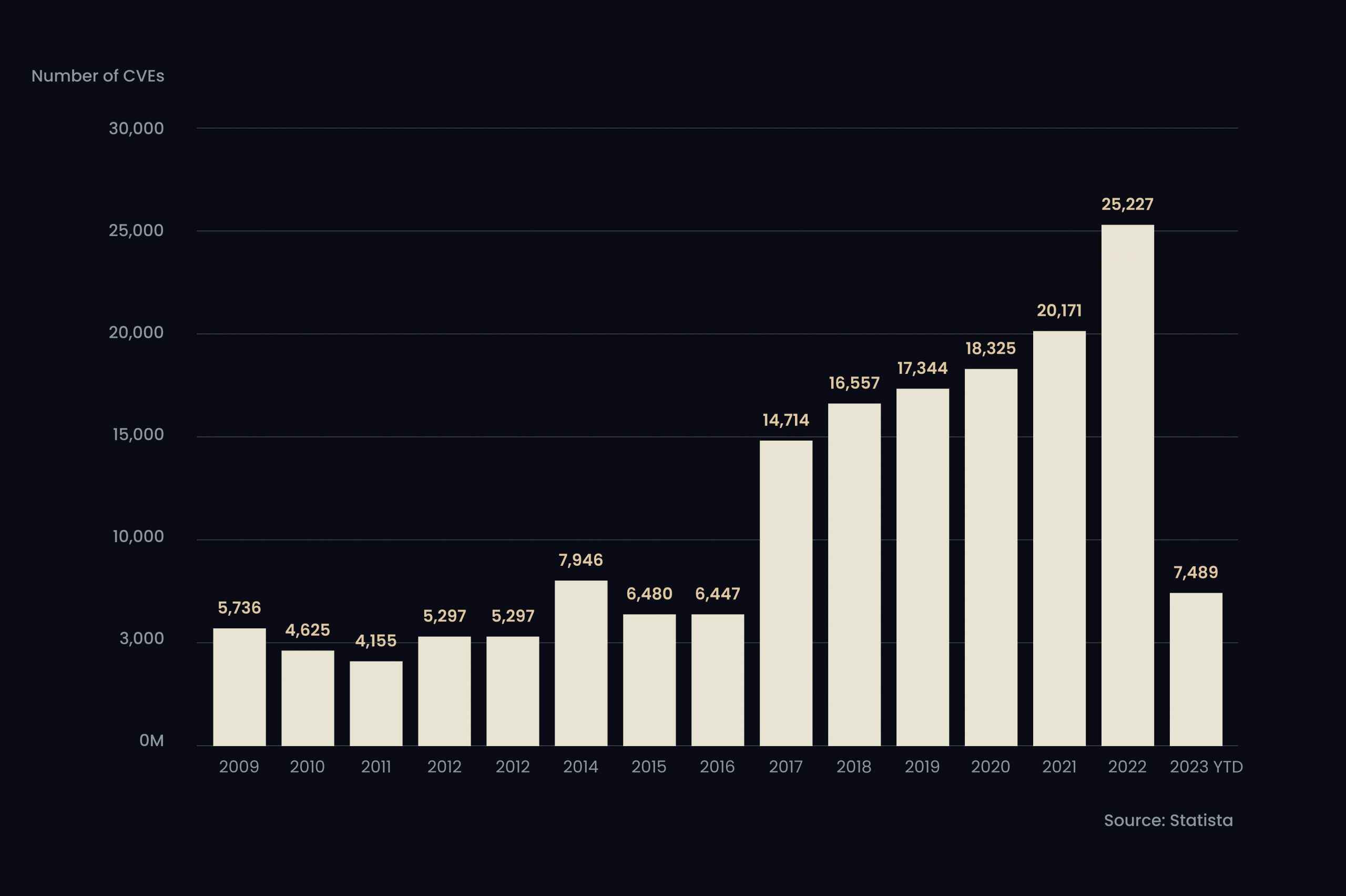
According to the latest data, Internet users found over 25,000 new common IT security flaws and exposures (CVEs) in 2022. Developers should fix that by implementing encryption and secure storage methods to protect customer data.
Other blunders appear as slip-ups. For instance, these are the lack of regular updates and system patching, infrequent testing for security vulnerabilities, and the absence of adequate user education. However, such challenges are a matter of your tech team’s responsible work.
Practice 3: Visibility and Restrictions of Functions
In terms of smart contracts, visibility refers to the level of access other contracts or users have to a particular function. Restrictions, on the other hand, are limitations on using certain functions.
Now, let’s briefly clarify how smart contracts work. These are self-executing algorithms executed automatically when particular conditions are met (for instance, a user performs a money-transferring order).
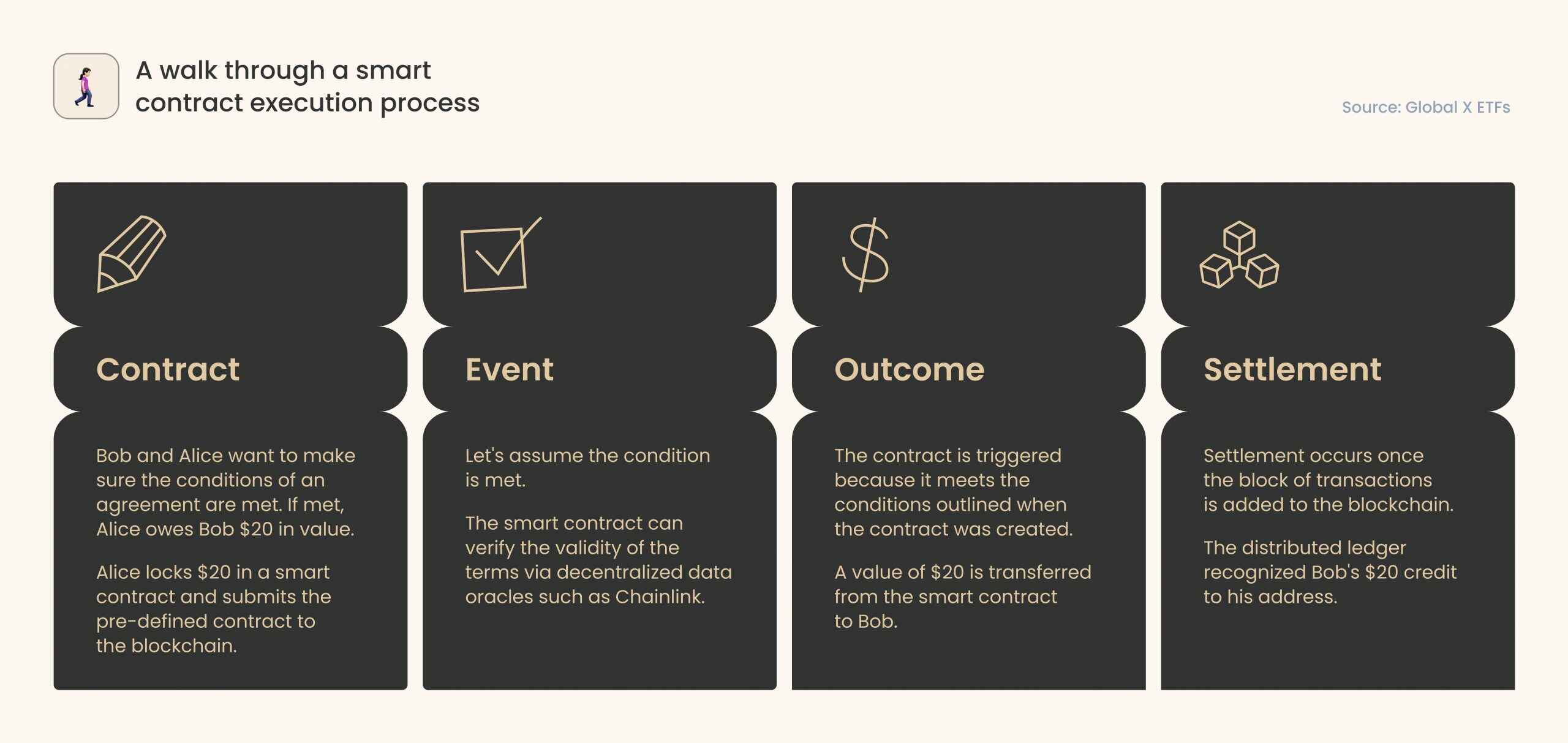
A common mistake developers often make when building smart contracts is making functions public without appropriate access controls. As a result, unauthorized users or contracts can access and manipulate the contract. To overcome this problem, your tech team should classify all functions as public, private, or internal, depending on their intended use and required access level.
Additionally, consider using access modifiers to restrict using certain functions. For example, “onlyOwner” or “onlyAdmin” can limit access to a particular function to specific roles or accounts. This way, you will prevent unauthorized access and reduce the risk of attacks.
Finally, make sure your tech team is aware of “reentrancy” attacks occurring when a function is repeatedly called before the previous call finishes. To prevent such attacks, the development team should implement relevant checkups and limitations on function calls.
Practice 4: Disaster Recovery Plan Creation
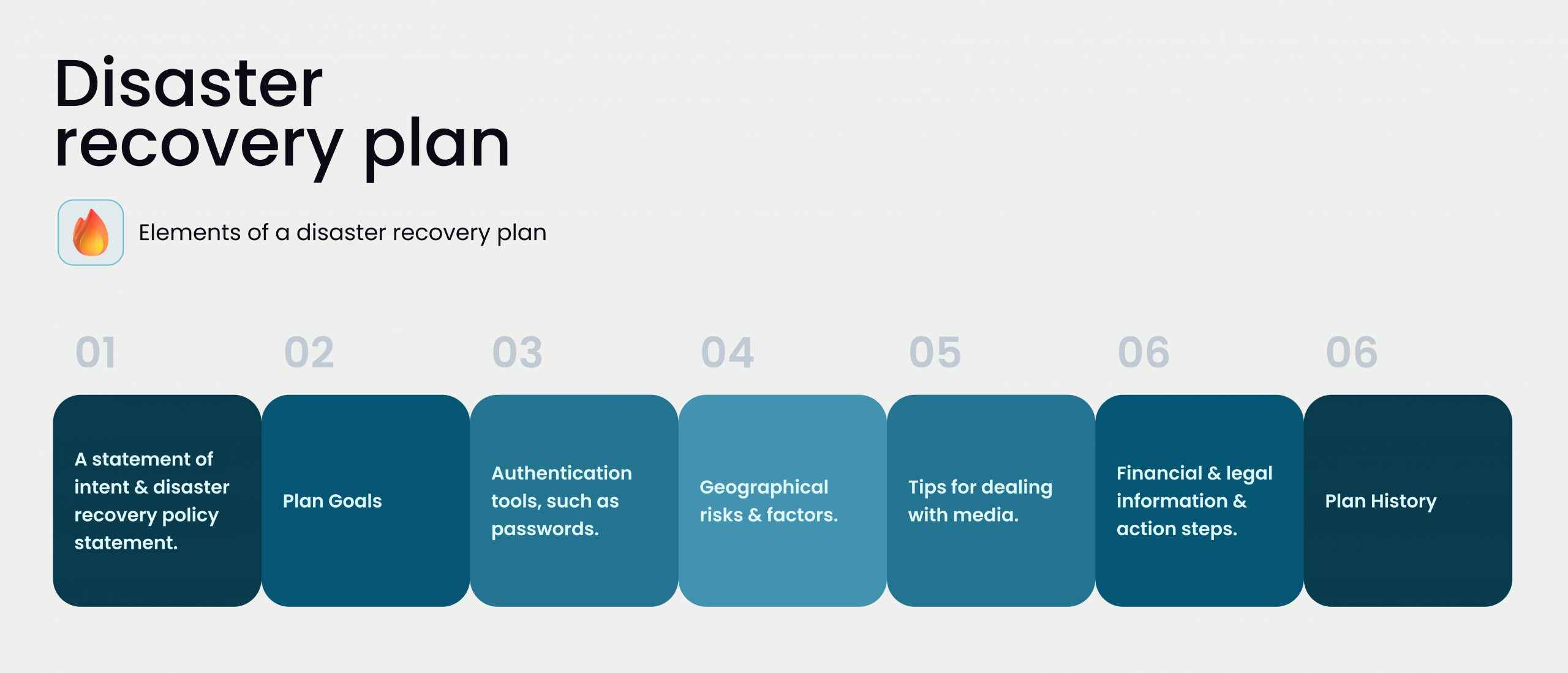
Catastrophes are usually unexpected and may strike anytime, be it a natural disaster, cyber-attack, or other threat. So to protect your system and user data, you need a well-designed disaster recovery plan. It suggests resistance to data loss and downtime. Thus, you can mitigate the impact of such events and ensure business stability if force-majeure events occur.
The first step in creating a disaster recovery plan is identifying potential risks and vulnerabilities. For that, assess the likelihood of various disasters and their potential impact on your blockchain project. When discovering threats, developers should do their best to prevent such events (for instance, by adding redundancy and backup systems).
Secondly, determine recovery objectives and develop a recovery strategy within your technical team. It involves establishing recovery time objectives (RTOs) and recovery point objectives (RPOs). This way, you will determine how quickly you can restore the system and how much data loss you can handle. Ensure your recovery strategy includes backup procedures, failover plans, and emergency procedures.
Finally, regularly test and update the disaster recovery plan to keep it practical and up-to-date. For example, conduct regular drills and simulations to test your plan’s efficiency and identify improvement areas during the checkup.
With a viable disaster recovery plan, you will know that your blockchain project remains safe and resistant to unexpected events. With a solid plan, your engineers can quickly recover the system and minimize the security challenges’ potential impact on your business.
5. Don’t Fall Victim to Reentrancy Attacks
As mentioned, a reentrancy attack occurs when a malicious actor calls a function on a smart contract repeatedly before the previous call has finished. As a result, they can steal funds or manipulate the contract’s state.
To protect your product against reentrancy attacks, your technical team should implement appropriate checks and restrictions on function calls. For instance, they can use the “require” keyword to check for conditions before executing a function, such as checking the contract’s balance or verifying if the call’s in progress.
Developers should also understand how external contracts interact with their smart contracts and take steps to limit their potential effect. For example, they can use “pull” payments instead of “push” ones. As a result, external contracts won’t be able to call a function continuously.
6. Randomness Source
Randomness is necessary for various functions in blockchain applications, like selecting validators, shuffling data, and generating cryptographic keys. However, relying on a weak or predictable source of randomness can leave your system vulnerable to cyber-attacks.
First, let’s quickly rewind the principles of centralized and decentralized transactions. Centralized transactions, be it banks in traditional finance or exchanges in We3, take full custody of their customers’ money. In contrast, a decentralized pattern relies on randomness, nodes, hashes, and more.
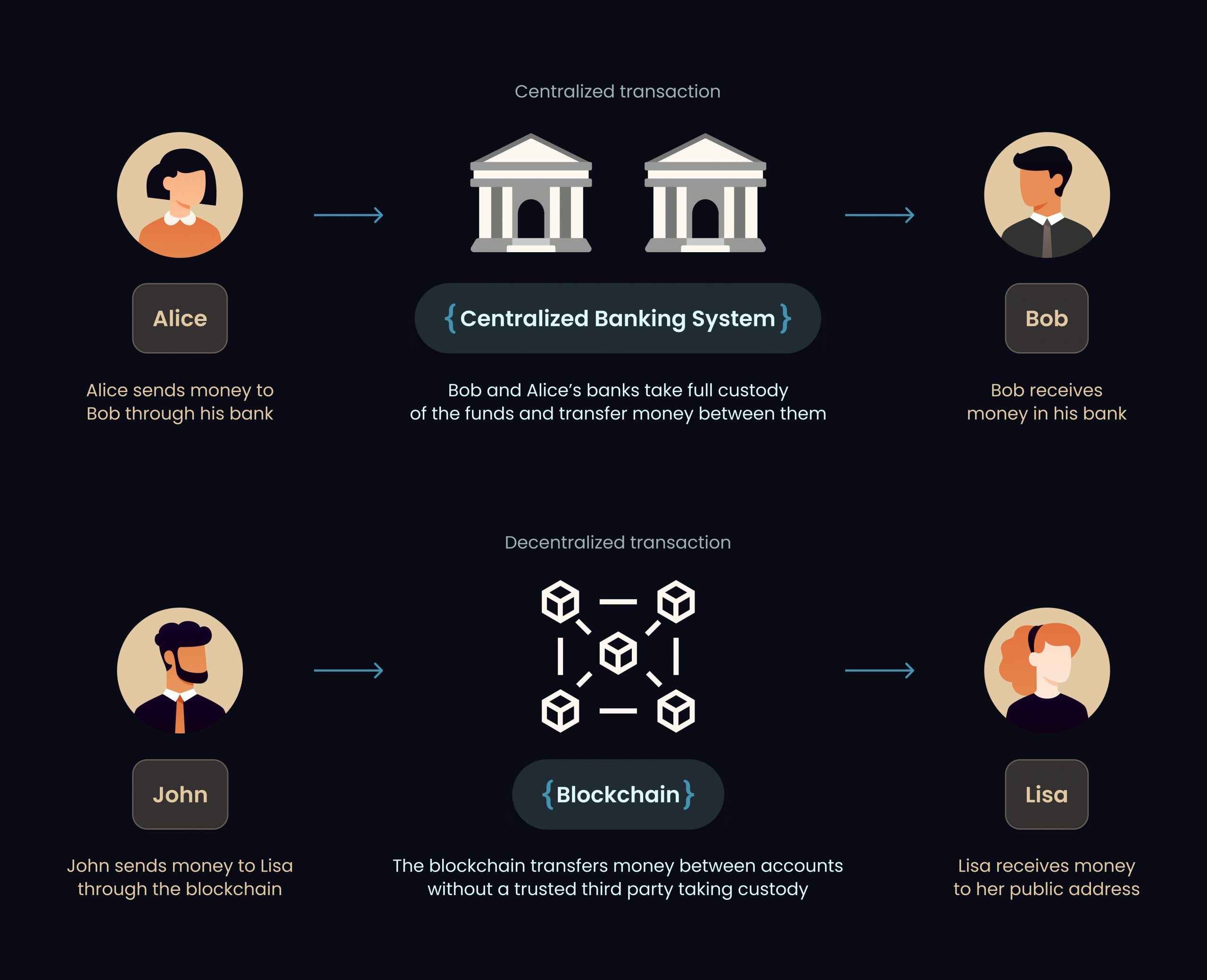
To safeguard randomness sources, developers can use trustworthy external sources, cryptographic hashes, or a verifiable delay function. Leverage cryptographic hashes create unpredictable outcomes, while a verifiable delay function may add a delay between requests, making it more difficult for attackers to predict outcomes.
Remember that using a source of randomness resistant to manipulation or prediction is critical. Developers should also take appropriate measures to eliminate the potential cybercriminals‘ impact on the randomness source.
Finally, conduct regular auditing and testing to identify weaknesses or vulnerabilities in the system’s randomness source. In particular, simulations or test cases help ensure that the source of randomness produces unpredictable and unbiased results.
7. External Audits for Mainnet Deployment
Before deploying a blockchain project to the mainnet, conducting an external audit is crucial. With its help, you will know if the system is secure, reliable, and meets industry standards.
If you need an external audit, hiring an independent security firm with deep expertise in blockchain security (like CertiK) is your way to go. Look for a smart contract auditor to conduct a comprehensive security review of the project’s code, architecture, and design. They should also identify potential vulnerabilities and weaknesses attackers may exploit.
The audit process includes:
- thoroughly analyzing the system’s code
- testing for common vulnerabilities
- providing recommendations on improving the system’s security
Meanwhile, an external audit report involves an assessment of the system’s overall security posture and tips on mitigating any identified risks.
Blockctreat’s data emphasizes the importance of audit. In 2020, losses from DeFi breaches totaled a startling $238M. It accounts for 41% of all blockchain-related occurrences in terms of value – all due to the audit’s inefficiency (or its complete absence).
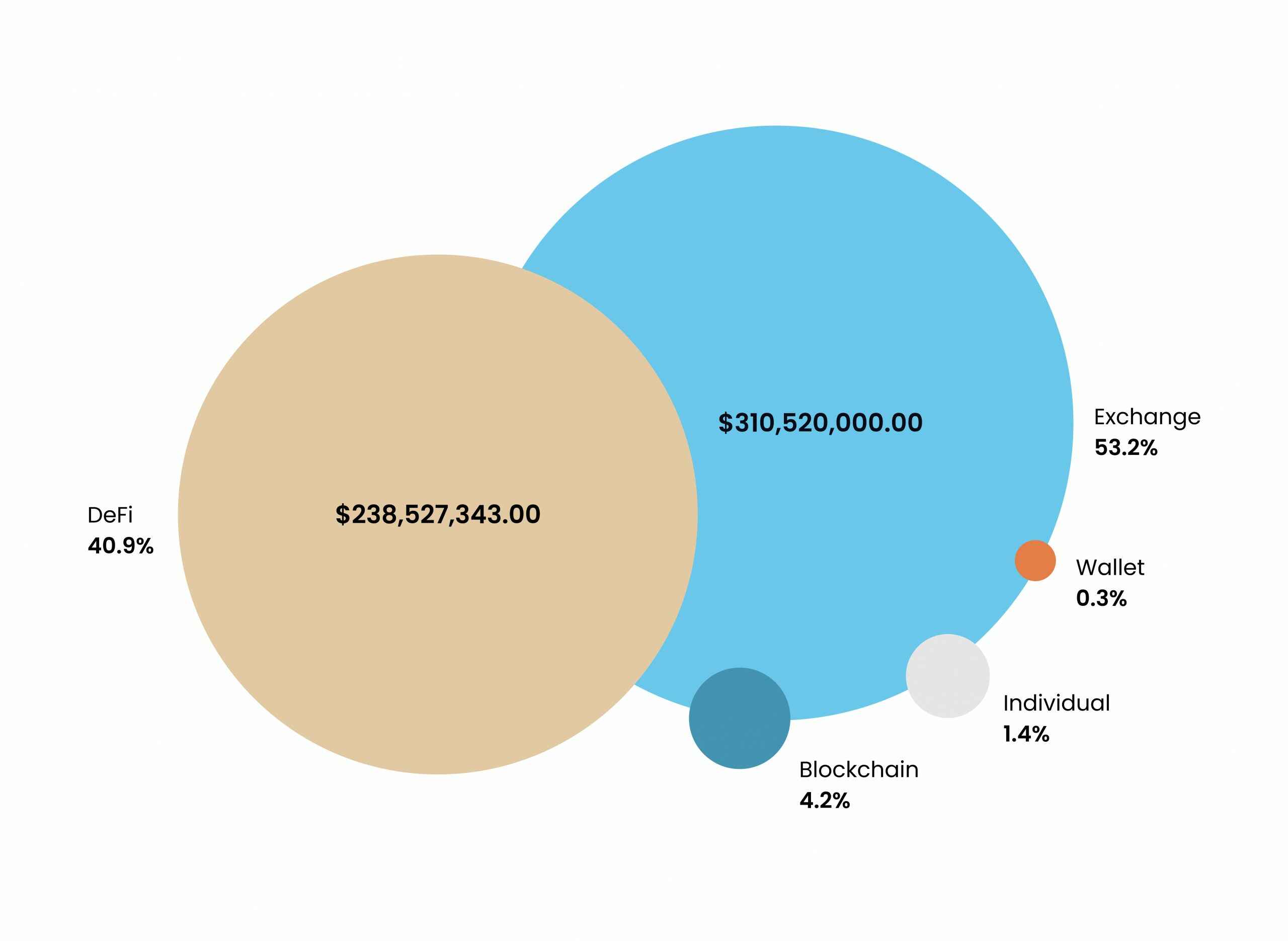
External audits provide an objective and independent review of the project’s security. It gives stakeholders confidence that the system is secure and trustworthy. Such checkups also help identify potential regulatory compliance issues and ensure that the project adheres to the core industry requirements.
Design Bulletproof dApps with WeSoftYou
The level of security DeFi products have inevitably depends on engineering team expertise. However, many other factors also matter, including architecture model, type of application, and even the hacker’s proficiency. Unfortunately, it’s impossible to create a comprehensive list of all possible vulnerabilities. But the realm of Web3 is witnessing new and advanced forms of decentralized finance use cases. And threat actors come up with new ways to compromise them.
Therefore, the DeFi community should collaborate in identifying and addressing these emerging risks throughout the entire ecosystem. Web3’s community-driving force constantly offers improved security practices. And you can leverage those methods to the fullest by hiring a trusted vendor with proven experience in the niche.
Trust WeSoftYou as your reliable partner in developing a DeFi solution for your business. As a Clutch-recognized B2B sector top app developer, we implement the best security practices in our end-to-end blockchain development and integration services.
As a Top-5 Growing Companies List representative, WeSoftYou has developed many successful projects within different industries. In particular, we have three years of experience in Web3 development. Here are some of the most notable projects we worked on.
NDAX
NDAX is a Canadian-based cryptocurrency trading platform. Its core objective is to offer users a safe, secure, and regulated means of trading crypto. Accordingly, the exchange complies with Canada’s banking regulations and adheres to the country’s highest security standards. These two criteria are crucial for a compliant and well-functioning crypto platform.
In terms of security, WeSoftYou provided full compliance with Canada’s banking regulations and AML policies. In particular, we integrated a seamless and user-friendly process of ID verification. Moreover, we continue to provide reliable, 24/7 customer support.
GoodDollar
The GoodDollar system aims to create, finance, and distribute basic income worldwide. It sets a minimum standard of living and reduces economic disparity by establishing a universal basic income (UBI). To ensure security, our team applied kiosks for visitor screening. Also, we integrated the platform with a cryptocurrency wallet to ensure fair income distribution. This way, our engineering team gave each client a personal touch while prioritizing KYC procedures.
Let us help you strengthen security in your dApp or develop a secure DeFi application from scratch. Contact us to discuss your particular project’s specifics.
FAQ
DeFi (Decentralized Finance) has robust security due to several factors. First and foremost, DeFi uses blockchain technology, which is inherently safe due to its decentralized and distributed nature. Traditional financial systems rely on central authorities (banks or governments). In contrast, blockchain-based DeFi apps are protected by a network of nodes that validate transactions and ensure the system’s integrity. This distributed and decentralized nature makes it challenging for hackers to manipulate or compromise the system.
In addition, DeFi also employs various security measures, such as smart contracts, multi-signature wallets, and permission access controls.
Smart contracts are self-executing contracts that automatically enforce agreements between parties without intermediaries’ involvement.
Multi-signature wallets require several signatures or approvals from authorized users before any transaction occurs.
Permission access controls limit access to certain functions or features of the app to authorized users only. It prevents unauthorized access and malicious activities.
Protecting a DeFi project requires implementing robust security measures and following best practices throughout the development lifecycle. Here are the essential methods to defend a DeFi project:
Conducting a thorough security audit. It’s an essential step in identifying vulnerabilities and potential risks in a DeFi project. It involves reviewing the project’і codebase and architecture, testing for potential exploits, and recommending improvements.
Implementing multi-factor authentication (MFA). MFA requires users to provide multiple forms of identification before accessing an application. Implementing it can prevent unauthorized access to a DeFi project.
Following secure smart contract development practices. As smart contracts are the backbone of most DeFi projects, it’s essential to follow the key security practices. For instance, these are using well-audited and tested code, implementing proper access controls, and testing for potential exploits.
Employing a multi-signature wallet. Such a wallet requires multiple approvals before executing any transaction. It helps prevent unauthorized transactions and reduce the risk of hacks.
Regular updates and system patching. These practices are crucial for fixing any vulnerabilities or bugs attackers may exploit.
Ensuring adequate training and education for users. As a product owner, you should ensure your users adopt strong passwords. Thus, they will avoid phishing scams and keep their devices secure.
It’s crucial to stick to the primary security standards throughout development and overall DeFi security best practices when building a blockchain project. Trust WeSoftYou to be your reliable partner in improving blockchain security. To provide security compliance, we conduct regular audits, provide multi-factor authentication (MFA), and develop well-protected smart contracts. Also, we come up with encryption and secure storage techniques. Finally, our team offers user education and training. Moreover, we constantly update and patch the system to guarantee its ultimate invulnerability.
All these measures reduce the chance of assaults, prevent unauthorized access, and guarantee user data security.